-
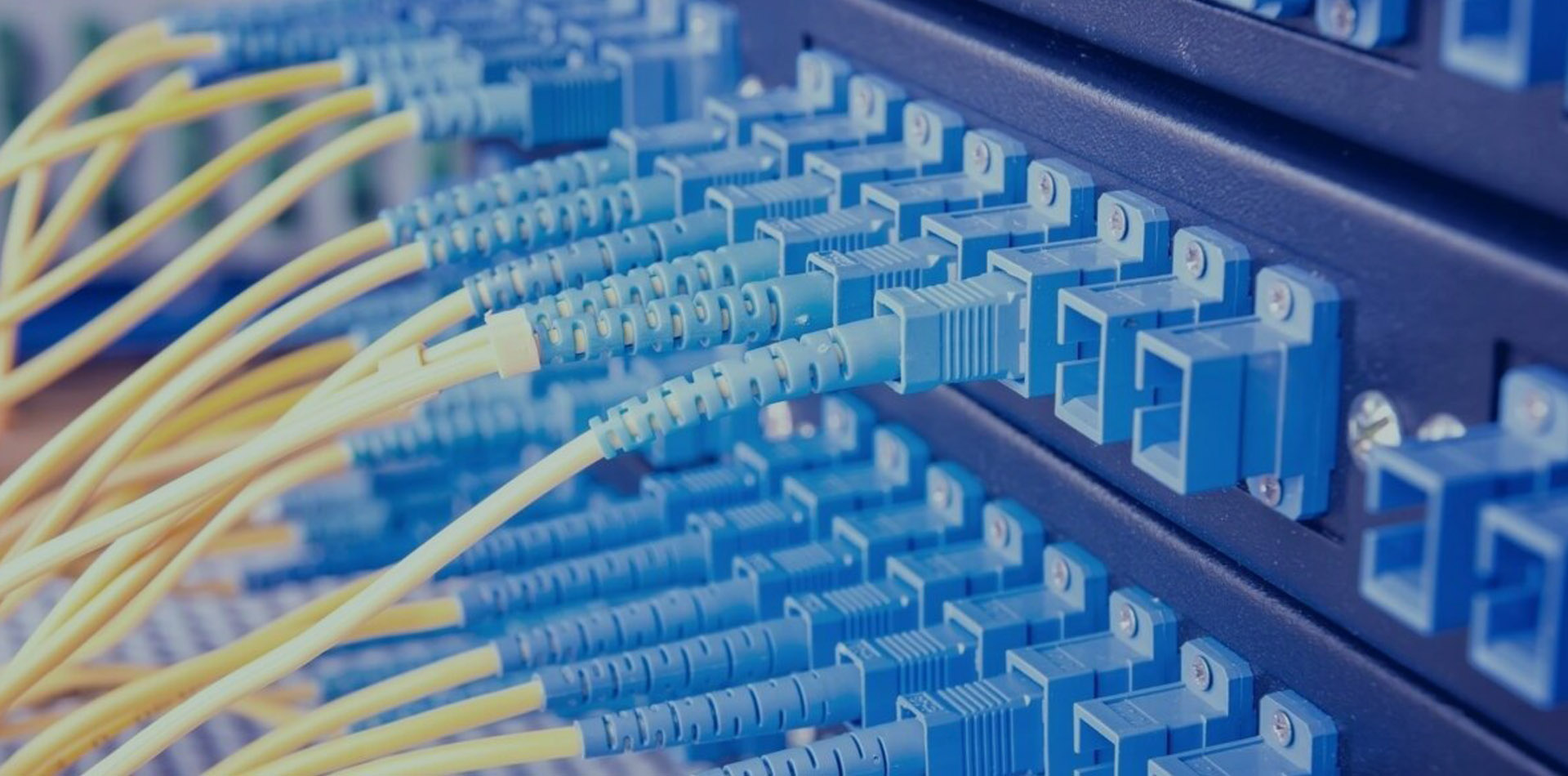 STRUCTURED CABLING SYSTEMSTHE PERFECT PARTNER FOR YOU
STRUCTURED CABLING SYSTEMSTHE PERFECT PARTNER FOR YOU -
 NETWORKING & TELECOM SYSTEMSTHE PERFECT PARTNER FOR YOU
NETWORKING & TELECOM SYSTEMSTHE PERFECT PARTNER FOR YOU -
 SECURITY SYSTEMSTHE PERFECT PARTNER FOR YOU
SECURITY SYSTEMSTHE PERFECT PARTNER FOR YOU -
 WIRELESS NETWOKING SYSTEMSTHE PERFECT PARTNER FOR YOU
WIRELESS NETWOKING SYSTEMSTHE PERFECT PARTNER FOR YOU -
 ACCESS CONTROL SYSTEMSTHE PERFECT PARTNER FOR YOU
ACCESS CONTROL SYSTEMSTHE PERFECT PARTNER FOR YOU -
 CLOUD COMPUTINGTHE PERFECT PARTNER FOR YOU
CLOUD COMPUTINGTHE PERFECT PARTNER FOR YOU
Data Security
Protecting data from unauthorized access and data corruption
Being in the most vulnerable computing world, cyber security world make sure all the data that your organization collects, stores, creates, receives or transmit are being protected from theft or manipulated. We can certainly help you to safeguard the data.
Cloud data security | Hardware security module | Authentication | Access Control | Backups & Recovery | Data masking | Email Security | Enterprise data protection | Data deletions & Ensure
